Incident Response Plan: Preparing for the Inevitable

Incident Response Plan: Defining Scope
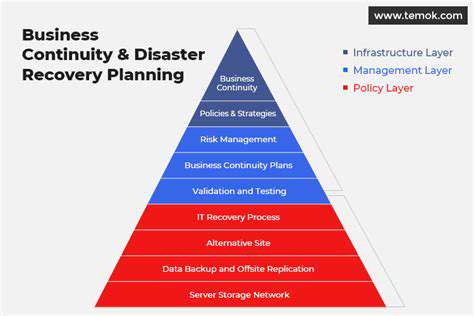
A comprehensive incident response plan (IRP) is crucial for any organization. It outlines the procedures and responsibilities for handling security incidents, from initial detection to containment and recovery. Defining the scope is the first and arguably most critical step in developing an effective IRP. This involves identifying the types of incidents to be addressed, the systems and assets that are within the scope, and the specific roles and responsibilities of personnel involved.
This initial phase should also consider factors like legal and regulatory requirements that might apply to the incident response process. It's essential to be clear about the organization's acceptable level of risk and the potential impact of various incidents. This will help determine the appropriate level of resources allocated to the IRP.
Incident Response Plan: Proactive Measures
Proactive measures, often overlooked, are vital for preventing incidents. These preventive measures include robust security controls, regular vulnerability assessments, and employee training on security awareness. Implementing these measures can significantly reduce the likelihood of a security incident occurring.
Regular security audits and penetration testing help identify and address potential weaknesses in systems and applications. These assessments are crucial for ensuring that the organization's security posture aligns with best practices and emerging threats.
Strong security awareness training is also essential. Employees are often the first line of defense against cyber threats, and training empowers them to recognize and report suspicious activity. This proactive approach can prevent a lot of potential incidents.
Incident Response Plan: Detection and Analysis
A critical component of an effective incident response plan is the early detection and analysis of security incidents. This includes implementing robust security monitoring tools and establishing clear escalation procedures for suspicious activity.
Establishing clear communication channels and procedures for reporting and escalating incidents is crucial for quick and efficient handling.
The analysis phase involves gathering information from various sources, including logs, alerts, and reports. This information helps determine the nature and scope of the incident.
Incident Response Plan: Containment and Eradication
Once an incident is detected and analyzed, the next crucial step is containment and eradication. This involves isolating the affected systems and assets to prevent the incident from spreading further. Effective containment strategies are essential to limit the damage caused by the incident.
Careful planning of eradication strategies is essential. This includes restoring systems to a known good state while avoiding any data loss or further damage. Choosing the right tools and procedures for eradicating the malicious code or threat is a critical part of the incident response process.
Incident Response Plan: Recovery and Lessons Learned
Following containment and eradication, the recovery phase focuses on restoring systems and services to their normal operational state. This phase also necessitates a careful review of the incident's impact and the effectiveness of the response plan.
Identifying the root cause of the incident is vital for preventing similar incidents in the future. Thorough documentation and analysis of the incident are essential to refine and improve the IRP for future use.
Incident Response Plan: Communication and Reporting
Effective communication is paramount throughout the incident response process. Clear communication channels and procedures are needed to inform stakeholders, such as management, affected users, and external parties (e.g., law enforcement or regulatory bodies), about the incident and the response efforts. This includes informing affected users of the incident and any steps they need to take to protect themselves.
Comprehensive incident reports should be documented, detailing the incident's timeline, impact, and response actions. These reports are essential for improving the IRP and for regulatory compliance.