Proactive Strategies for Security
Proactive security measures are crucial for mitigating potential threats and vulnerabilities. Instead of simply reacting to incidents after they occur, proactive strategies focus on identifying and addressing potential risks before they escalate. This approach often involves a combination of technical safeguards, robust policies, and employee training. Implementing a strong security culture is paramount to ensuring long-term protection. Proactive security measures encompass a wide range of activities, from regular vulnerability assessments to the development and enforcement of strict security protocols.
Effective proactive security measures require a holistic approach that considers both internal and external threats. This includes understanding the potential entry points for malicious actors, identifying vulnerabilities in systems and processes, and implementing controls to mitigate those risks. Companies must invest in security awareness training to empower employees to recognize and report suspicious activities. Regularly updating security software and hardware is also a fundamental part of a proactive security strategy.
Building a Robust Security Infrastructure
A robust security infrastructure is the foundation upon which a strong security posture is built. This involves implementing various security controls, such as firewalls, intrusion detection systems, and antivirus software. These controls work together to create a layered defense, making it significantly harder for attackers to penetrate the system. Thorough configuration management is essential for ensuring that security controls are properly implemented and maintained.
Implementing a strong security information and event management (SIEM) system is also vital. A SIEM system allows for centralized monitoring and analysis of security events, providing valuable insights into potential threats. A robust incident response plan is also necessary for handling security incidents effectively and minimizing the impact on operations. This plan should be regularly reviewed and updated to reflect evolving threats and vulnerabilities.
Employee Training and Awareness
Employee training and awareness programs are essential components of a comprehensive security strategy. Employees are often the first line of defense against cyber threats, and educating them about common threats, phishing scams, and social engineering tactics is crucial. Providing regular training sessions can significantly improve employees' ability to recognize and report suspicious activities. Training should cover a wide range of topics, including password security best practices, safe internet browsing habits, and the importance of reporting potential security breaches.
Encouraging a culture of security awareness and responsibility among employees is key to success. This means fostering an environment where employees feel comfortable reporting suspicious activities without fear of reprisal. Regular communication and updates about security threats and best practices will further enhance employee awareness and participation in maintaining a secure environment. It is vital to make security a shared responsibility, not just the responsibility of the IT department.
Robust Detection: Identifying and Containing Threats
Advanced Threat Detection Techniques
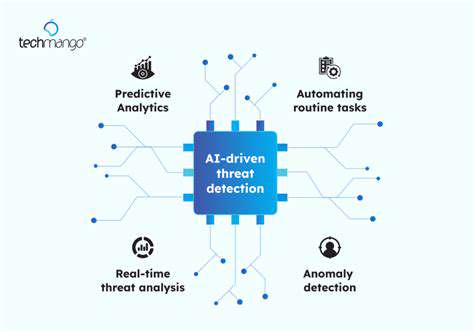
Robust detection of ransomware threats requires a multi-layered approach that goes beyond basic antivirus software. Employing advanced threat detection techniques, such as machine learning algorithms and behavioral analysis, is crucial. These sophisticated methods can identify subtle anomalies in system activity, potentially signaling a ransomware attack before significant damage occurs. This proactive approach allows for swift containment and minimizes the potential for widespread infection.
Real-time monitoring of network traffic is another critical component of advanced threat detection. By actively analyzing data streams, security systems can identify suspicious patterns and connections, potentially revealing the initial point of intrusion. This enables rapid isolation of compromised systems and prevents further propagation of the threat throughout the network.
Proactive Security Measures
Beyond detection, proactive security measures are essential for mitigating the risk of ransomware attacks. Implementing robust security protocols, such as strong password policies and multi-factor authentication, can significantly reduce the attack surface. Regular security assessments and vulnerability scans can identify weaknesses in systems and applications before they are exploited.
Regularly updating software and operating systems is also critical. Patching vulnerabilities promptly can prevent attackers from leveraging known exploits to gain unauthorized access. Maintaining current security tools and configurations ensures that the security posture is constantly adapted to evolving threats.
Containing the Spread of Infection
Even with robust detection measures in place, containing the spread of ransomware infection is paramount to minimizing damage. Implementing network segmentation can limit the impact of a breach by isolating compromised systems from the rest of the network. Having a documented incident response plan is also crucial; this plan should detail the steps to be taken in case of an attack, ensuring that the organization can respond effectively, swiftly, and methodically.
Having regular backups of critical data is another important component of containing the spread. Regular backups, stored in a secure and isolated location, provide a recovery mechanism in case of infection. This ensures that business operations can be restored quickly and minimize disruption.
Incident Response and Recovery
A well-defined incident response plan is critical for mitigating the damage caused by a ransomware attack. This plan should outline the procedures for containing the threat, isolating affected systems, and restoring data from backups. A clear communication strategy is also essential to keep stakeholders informed and minimize panic during the crisis.
Collaboration between IT security teams, legal counsel, and business continuity teams is essential during incident response. Effective communication and coordination are vital for a swift and efficient recovery process. Lessons learned from the incident should be documented and implemented to prevent future occurrences.
Data Backup and Recovery: Ensuring Business Continuity
Understanding the Importance of Data Backup
Data backup is a critical aspect of any business operation, especially in today's digital landscape. Losing critical data can lead to significant financial losses, reputational damage, and operational disruptions. A well-defined data backup strategy safeguards your business's valuable information, ensuring business continuity and minimizing the impact of potential disasters, such as ransomware attacks, hardware failures, or human errors. Proper backup procedures are essential for restoring operations swiftly and efficiently.
Implementing a robust data backup solution is not just about preventing data loss; it's about safeguarding your business's future. This proactive measure allows you to quickly recover from unforeseen circumstances, ensuring minimal downtime and maintaining productivity. By regularly backing up your data, you are effectively mitigating the risks associated with data breaches, accidental deletions, or natural disasters.
Choosing the Right Backup Method
Selecting the appropriate backup method is crucial for effective data protection. Consider factors like the size of your data, the frequency of changes, and the resources available. Cloud-based backup solutions offer scalability and accessibility, while on-site solutions provide faster recovery times. Hybrid approaches combining both cloud and on-site backups can offer the best of both worlds, providing redundancy and flexibility.
Evaluating your specific needs and resources is key to selecting a backup method that aligns with your business's requirements. Consider the speed of recovery you need, the potential for data corruption, and the cost-effectiveness of different solutions. A thorough analysis will help you choose the optimal strategy to ensure your data remains safe and readily available.
Implementing a Regular Backup Schedule
Establishing a consistent and regular backup schedule is paramount for maintaining data integrity. Defining specific intervals for backing up data, such as daily, weekly, or monthly, is essential for minimizing the risk of data loss. This proactive approach ensures that recent data is always protected, minimizing the impact of any unforeseen events.
Regular backups prevent data loss from accumulated changes, ensuring that you always have a recent copy of your critical files. A well-defined schedule also helps in determining how long you need to retain backup copies. This proactive approach is essential for maintaining your business's operational resilience.
Testing Your Backup and Recovery Procedures
Regular testing of your backup and recovery procedures is vital for ensuring that your systems function correctly. Simulated data loss scenarios can help you identify potential weaknesses in your backup strategy and pinpoint areas needing improvement. This proactive approach allows you to address any shortcomings before they lead to actual data loss.
Data Security in Backup Systems
Data security is paramount when it comes to backup systems. Implementing strong encryption protocols, access controls, and secure storage methods is crucial to prevent unauthorized access to your valuable data. This proactive measure safeguards sensitive information from potential threats, minimizing the risk of data breaches and ensuring the confidentiality of your backups.
Recovery Planning and Disaster Response
Developing a comprehensive recovery plan is essential for ensuring a smooth transition in the event of a data breach or disaster. This plan should outline the steps required to restore your data and systems, including contact information for key personnel and the recovery timeline. Having a well-defined plan allows your business to respond effectively to a crisis, minimizing downtime and maintaining business continuity.
Data Retention Policies and Compliance
Establishing clear data retention policies is vital for ensuring compliance with relevant regulations. These policies should outline how long backups are retained and how they are managed. Adhering to these policies not only ensures regulatory compliance but also helps optimize storage space and maintain data integrity. A well-defined policy provides a framework for managing data and ensures that sensitive information is handled responsibly.
Employee Training and Awareness: Educating the Human Element
Understanding the Importance of Employee Training
Employee training and awareness programs are crucial for creating a robust security posture within any organization. These programs aren't just about ticking boxes; they're about fostering a culture of vigilance and responsibility. By equipping employees with the knowledge and skills to identify and report potential risks, organizations significantly enhance their defenses against various threats. This proactive approach goes beyond simply reacting to incidents; it instills a proactive mindset that anticipates and mitigates potential issues before they escalate.
A well-structured training program addresses not only technical vulnerabilities but also the human element, which is often the weakest link in a security chain. This includes educating employees about social engineering tactics, phishing attempts, and the importance of secure passwords and access controls.
Recognizing Common Threats and Vulnerabilities
Employees need to understand the various threats they might encounter in their daily work. Phishing emails, malware disguised as legitimate attachments, and malicious websites are just a few examples of the sophisticated tactics used by cybercriminals. Training programs should cover the characteristics of these threats and equip employees with the ability to recognize and report suspicious activities.
Vulnerabilities in systems and processes must also be highlighted. This includes explaining how weak passwords, outdated software, and inadequate security protocols can expose the organization to risks. By understanding these vulnerabilities, employees can actively contribute to a more secure environment.
Implementing Effective Communication Strategies
Clear and concise communication is paramount in any training program. Employees need to understand the procedures for reporting suspicious activities or incidents promptly. The training materials should be easily accessible and consistently updated to reflect the evolving threat landscape. Regular reminders and updates ensure that employees remain vigilant and informed about emerging threats.
Establishing a Culture of Security Awareness
A strong security culture is built on a foundation of awareness and shared responsibility. Training should go beyond simply presenting information; it should foster a sense of ownership and encourage employees to actively participate in maintaining a secure environment. Creating a culture of security awareness means emphasizing the importance of vigilance and the potential consequences of negligence.
Focusing on Practical Application and Exercises
Theory alone isn't enough to create effective security awareness. Hands-on exercises and simulations are essential to reinforce the concepts learned and demonstrate their practical application. These exercises should simulate real-world scenarios, allowing employees to practice identifying and responding to potential threats in a safe environment. Interactive training modules that incorporate gamification can make the learning process more engaging and memorable.
Addressing Specific Roles and Responsibilities
Different roles within an organization will have varying levels of exposure to security risks. Tailoring training programs to specific job functions ensures that employees receive the most relevant and applicable information. For example, customer service representatives need training on recognizing phishing attempts and preventing data breaches, while IT staff require specialized knowledge about system vulnerabilities and security protocols. This targeted approach strengthens the overall security posture.
Evaluating Training Effectiveness and Continuous Improvement
Regular evaluation of training programs is crucial to assess their effectiveness and identify areas for improvement. Feedback mechanisms, post-training assessments, and regular security awareness campaigns are all crucial components of a robust training strategy. Continuous improvement ensures that training programs remain current and relevant, addressing emerging threats and evolving security protocols. Employee feedback is essential to ensure the program remains effective.
Incident Response Plan: Preparing for the Worst

Incident Response Planning: A Foundation for Success
A robust incident response plan is crucial for any organization. It provides a structured framework for handling security incidents, minimizing damage, and ensuring a swift and effective recovery. Proactive planning is key to mitigating potential risks and ensuring business continuity. A well-defined plan outlines roles, responsibilities, and procedures for various incident types, ensuring everyone understands their part in the process.
Developing a comprehensive incident response plan requires careful consideration of potential threats and vulnerabilities. This includes identifying critical systems and data, assessing potential risks, and establishing clear communication channels. Thorough preparation is essential for a successful response.
Defining Incident Types and Scope
This section clearly defines different types of security incidents, ranging from malware infections and data breaches to denial-of-service attacks and phishing attempts. It's important to categorize incidents based on severity and impact to prioritize responses effectively.
Understanding the scope of the incident is equally important. This involves pinpointing the affected systems, data, and users, as well as identifying the potential ripple effects and cascading impacts on the wider organization.
Establishing Communication Channels and Procedures
Clear communication is vital during an incident response. This section outlines the communication protocols, contact lists, and escalation procedures for different incident levels. Efficient communication is crucial for coordinating the response and keeping stakeholders informed.
Designated personnel or teams should be responsible for communication with affected parties, the media, and regulatory bodies. This ensures timely and accurate information dissemination.
Incident Response Team Structure and Roles
Defining the incident response team and outlining individual roles and responsibilities is essential. This includes designating a leader, analysts, communicators, and technical specialists. A well-defined structure ensures effective and coordinated action.
Establishing clear lines of authority and responsibility minimizes confusion and ensures that the response effort remains focused and efficient. This is vital for maintaining control and consistency throughout the process.
Developing Procedures for Containment, Eradication, and Recovery
This section details the procedures for containing the incident, eradicating the threat, and recovering affected systems and data. These procedures should be clearly defined and documented for consistent execution.
Each procedure should be detailed, covering the steps involved, the resources needed, and the expected timeframe for completion. Regular reviews and updates are essential to maintain the plan's effectiveness.
Maintaining Documentation and Reporting
Detailed documentation of the incident response process is critical for post-incident analysis, lessons learned, and compliance requirements. This includes logging all actions taken, communication records, and any affected systems or data. This meticulous record-keeping is invaluable for future incident prevention and improvement.
Regular reporting and analysis of incident response activities are essential for identifying trends and improving the organization's overall security posture. This continuous monitoring process fosters a culture of proactive security.
Testing and Updating the Incident Response Plan
Regular testing and updating of the incident response plan are critical for maintaining its relevance and effectiveness. This includes simulating real-world incidents to evaluate the plan's strengths and weaknesses and identify areas for improvement. This iterative process ensures that the plan is always current and capable of handling various scenarios.
Regular updates to the plan should incorporate lessons learned from previous incidents, changes in the threat landscape, and evolving technologies. This ensures that the plan remains current and effective in addressing emerging risks.