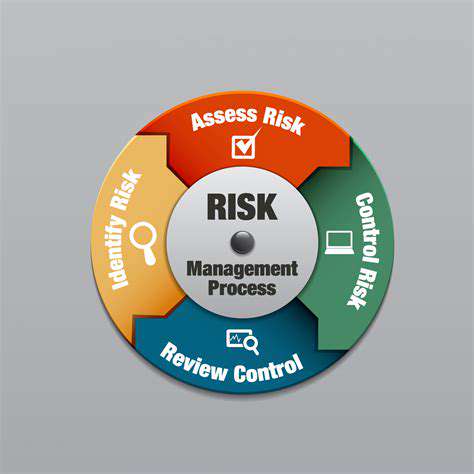
Robust security measures are essential to mitigate the risks associated with the evolving threat landscape in retail IoT. A multi-layered approach encompassing device security, network security, and data security protocols is paramount. Implementing strong authentication and authorization measures for all IoT devices is crucial, along with regular security audits and vulnerability assessments.
Furthermore, implementing robust encryption protocols for data transmission and storage is critical. This includes using end-to-end encryption for customer data and implementing data loss prevention (DLP) measures. Security training for employees and continuous monitoring of system activity are also essential components of a comprehensive security strategy.

Securing Customer Data in the IoT Ecosystem
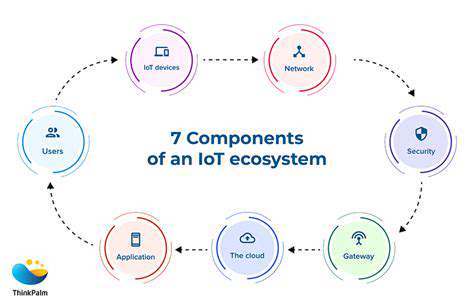
Protecting Against Data Breaches
In the increasingly interconnected world of the Internet of Things (IoT), the security of customer data is paramount. Protecting sensitive information from malicious actors is crucial, as breaches can have devastating consequences for both individuals and organizations. IoT devices often collect and transmit vast amounts of personal data, making them attractive targets for cybercriminals. This data, which can include financial information, health records, and location data, must be safeguarded with robust security measures to prevent unauthorized access and exploitation. Effective security protocols are essential to maintaining customer trust and preventing reputational damage.
Robust data encryption methods are essential to ensure that data remains confidential even if intercepted. Implementing multi-factor authentication is another critical step in strengthening security. By requiring multiple forms of verification, like a password and a code sent to a mobile device, unauthorized access attempts are significantly thwarted. Furthermore, regular security audits and penetration testing are crucial to identifying and patching vulnerabilities before they can be exploited. These proactive measures can help prevent data breaches and mitigate the potential consequences.
Implementing Secure Communication Protocols
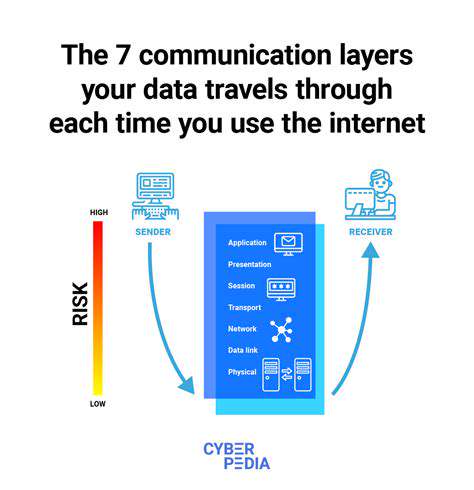
Secure communication protocols are fundamental to protecting data transmitted between IoT devices and the cloud. Using encryption protocols like TLS/SSL is vital to ensure that data remains confidential. These protocols encrypt data in transit, making it unreadable to anyone intercepting the communication. This is particularly important for sensitive data like credit card details or medical records. Additionally, choosing secure communication channels for data transfer and storage is critical. This includes verifying the security of cloud platforms and ensuring that they adhere to industry best practices.
Data integrity is also paramount. Ensuring the data is not tampered with during transmission is crucial. Implementing mechanisms like digital signatures can help verify the authenticity and integrity of the data. Additionally, secure authentication measures for devices and users are essential to prevent unauthorized access. This includes using strong passwords, implementing two-factor authentication, and regularly updating device firmware.
Developing Strong Security Policies and Procedures
Developing and enforcing strong security policies and procedures is essential for protecting customer data in the IoT environment. These policies should cover everything from data encryption and access controls to incident response procedures. A robust security policy should address the potential for vulnerabilities in IoT devices and the protocols for managing those vulnerabilities. Regular security awareness training for employees is also critical to ensure that they understand and follow security protocols. This training can help prevent human error, which is a significant factor in many data breaches.
Incident response plans are critical for dealing with potential security breaches. Having a documented plan in place allows for a swift and organized response to an incident. This includes clear procedures for identifying, containing, and recovering from a data breach. This proactive approach can minimize the impact of a security incident and help restore trust with customers.
Regular security audits and penetration testing are essential to identify weaknesses in the security infrastructure. These measures help proactively address vulnerabilities and ensure the ongoing security of customer data. Regular updates to security protocols and software are also crucial to maintaining protection against emerging threats.
Staying Ahead of the Curve: Continuous Monitoring and Adaptation
Understanding the Evolving Threat Landscape
The Internet of Things (IoT) is rapidly expanding, connecting billions of devices and creating unprecedented opportunities for innovation. However, this interconnectedness also introduces new and evolving security risks. Malicious actors are constantly developing sophisticated techniques to exploit vulnerabilities in IoT devices, from simple denial-of-service attacks to sophisticated data breaches. Understanding the evolving nature of these threats is crucial for organizations to implement effective security measures and protect their systems and data.
Staying ahead of the curve requires a proactive approach to threat intelligence. This involves monitoring emerging threats, analyzing attack vectors, and adapting security strategies to mitigate risks. Organizations must be aware of not only the traditional cybersecurity threats but also the unique vulnerabilities associated with IoT devices, such as their often-limited processing power and lack of robust security protocols.
Implementing Continuous Monitoring Systems
Effective IoT security relies heavily on continuous monitoring. This involves deploying robust security tools and technologies that provide real-time visibility into network traffic, device activity, and potential security breaches. Implementing sophisticated intrusion detection systems (IDS) and intrusion prevention systems (IPS) is critical for identifying and responding to malicious activities as they occur.
Furthermore, continuous monitoring necessitates the use of log analysis tools to identify patterns and anomalies that could signal a security incident. These systems must be able to correlate data from various sources, including network logs, device logs, and security information and event management (SIEM) systems, to provide a comprehensive view of the security posture.
Continuous monitoring also includes automated threat detection and response mechanisms. These systems should be capable of automatically identifying and mitigating threats in real-time, minimizing the impact of potential attacks.
Adapting Security Strategies for Dynamic Environments
The IoT environment is constantly changing, with new devices and applications emerging regularly. Security strategies must be adaptable to accommodate these changes. This adaptability requires a flexible and scalable security framework that can be adjusted to address new vulnerabilities and threats as they arise. A crucial component of this adaptability is the use of machine learning and artificial intelligence (AI) to identify and respond to emerging threats faster than traditional methods.
Prioritizing Proactive Security Measures
Proactive security measures are essential to maintaining a robust security posture in the IoT landscape. This involves implementing security best practices at every stage of the device lifecycle, from design and development to deployment and management. Implementing strong authentication and authorization protocols, along with encryption and secure communication channels, are vital to protect sensitive data and prevent unauthorized access.
Regular security audits and penetration testing are also critical proactive measures. These assessments can identify vulnerabilities that may not be immediately apparent, and help organizations implement patches and updates to address them before they can be exploited. Furthermore, robust employee training is crucial, as human error can often be the weakest link in any security system.