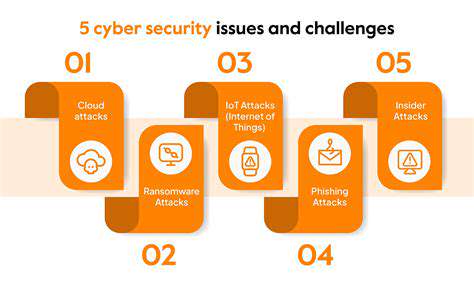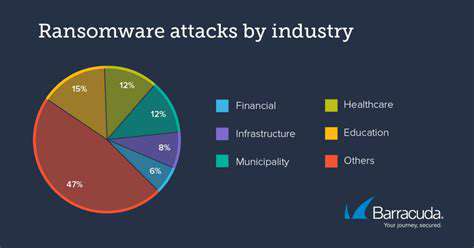
Identifying and Assessing Risks
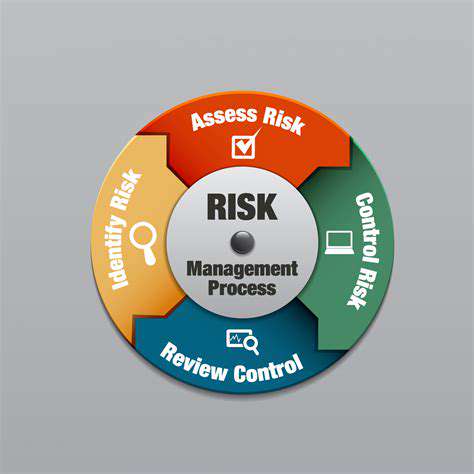
Understanding Risk Factors
Identifying potential risks is a crucial first step in effective risk management. A thorough understanding of the factors that can lead to negative consequences is essential. This involves analyzing internal and external influences, such as financial instability, market fluctuations, and technological advancements. Careful consideration must be given to the potential impact of these factors on the project or organization. By analyzing historical data and industry trends, organizations can proactively identify and assess potential risks.
Risk factors can stem from various sources, including operational inefficiencies, regulatory changes, and even unforeseen external events. Understanding these diverse potential triggers is fundamental to building a comprehensive risk assessment framework.
Qualitative Risk Assessment
Qualitative risk assessment focuses on identifying and prioritizing risks based on their likelihood and potential impact. This method often employs subjective judgment and expert opinions to determine the severity of different risks. It provides a valuable initial overview of the risk landscape, helping to quickly identify the most significant concerns. Qualitative assessment is often used as a preliminary step, followed by a more quantitative analysis.
This approach is particularly useful for projects with limited data or resources. It allows for a quick, flexible evaluation and helps prioritize risks for further investigation.
Quantitative Risk Assessment
Quantitative risk assessment moves beyond subjective estimations and delves into numerical data. This method utilizes statistical analysis and mathematical models to quantify the probability and impact of identified risks. This approach provides a more precise understanding of the potential financial or operational consequences of each risk. This detailed analysis enables organizations to make data-driven decisions about risk mitigation strategies.
Using historical data and statistical models, quantitative methods provide a more robust assessment, allowing for more informed decision-making.
Risk Response Planning
Once risks have been identified and assessed, the next crucial step is developing a response plan. This includes determining the best course of action for each identified risk. Effective risk response strategies can significantly reduce the negative impact of potential threats on operations. These strategies could include mitigation, avoidance, acceptance, or transference.
This planning process requires careful consideration of resources, timelines, and potential dependencies. It also involves clear communication and collaboration across different teams or departments within the organization.
Risk Monitoring and Control
Risk management is an ongoing process, not a one-time event. Continuous monitoring and control are essential to ensure that the identified risks are effectively managed. This involves regular review of the risk assessment, adjustments to the response strategies as needed, and ongoing communication. Proactive monitoring allows organizations to adapt to changing circumstances and potential new threats. This ensures that the organization remains prepared to address risks that may emerge over time.
Communication and Collaboration
effective risk management relies heavily on clear communication and collaboration among stakeholders. Open communication channels ensure that all relevant parties understand the identified risks, their potential impact, and the implemented mitigation strategies. Regular updates and shared insights are crucial for maintaining a common understanding of the risk landscape. Collaboration fosters a collective responsibility for risk management, creating a more robust and resilient organization.
This process involves regular reporting, meetings, and workshops to ensure that everyone is on the same page and working toward the same objectives.