Supply chain security has emerged as a significant concern. The reliance on third-party vendors and suppliers introduces new avenues for malicious actors to infiltrate sensitive systems. Compromised components, malicious code embedded in software updates, and even the theft of intellectual property from a supplier can have cascading effects on an organization's security posture. Proactively assessing the security posture of vendors and implementing stringent security protocols are critical steps to mitigate these risks.
Due diligence in supplier selection and ongoing monitoring of their security practices are essential. Building resilient supply chains that incorporate security as a core value throughout the entire process is crucial for preventing breaches and protecting sensitive information.
The Cloud Computing Conundrum: Securing Remote Resources
Cloud adoption has revolutionized business operations, but it also introduces unique security challenges. Data stored and processed in cloud environments can be vulnerable if not properly secured. Misconfigurations, unauthorized access, and data breaches can all stem from inadequate cloud security measures. A robust cloud security strategy is vital to protect data and applications residing in the cloud.
Remote Workforce and Mobile Devices: Enhancing Security Practices
The rise of remote workforces has created a new set of security challenges, as employees access company resources from various locations and devices. Ensuring secure remote access, managing mobile device security, and enforcing strong authentication protocols are critical to maintaining data integrity and confidentiality. Organizations must adapt their security policies to accommodate remote work while maintaining a high level of protection for sensitive information.
Educating employees on best practices for cybersecurity is essential. Raising awareness about phishing scams, password security, and other potential threats is crucial for mitigating risks associated with a dispersed workforce.
Protecting Sensitive Data Across the Extended Ecosystem
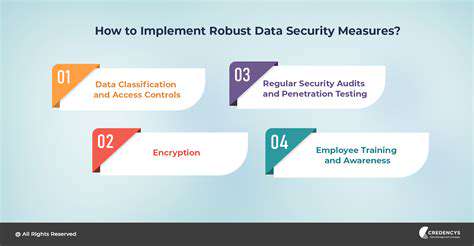
Data breaches can originate from any point in the extended ecosystem. Protecting sensitive data, regardless of its location, is paramount. Implementing robust encryption, access controls, and data loss prevention measures is essential for safeguarding information throughout the entire chain. Regular security assessments and penetration testing can help organizations identify and address weaknesses before they are exploited.
AI-driven platforms are revolutionizing education by creating personalized learning journeys tailored to individual student needs and preferences. These platforms analyze student performance data, learning styles, and even emotional responses to adapt the curriculum and pacing in real-time. This individualized approach fosters deeper engagement and understanding, ultimately boosting student success rates across various subjects and skill sets. Students can learn at their own pace, focusing on areas where they need more support while accelerating through concepts they grasp quickly. This customized learning experience significantly enhances the overall learning experience, fostering a more effective and enjoyable educational environment.
Embracing Advanced Technologies for Enhanced Visibility and Control

Leveraging Artificial Intelligence
Artificial intelligence (AI) is rapidly transforming various sectors, and its integration into business operations is becoming increasingly crucial. AI-powered tools can automate repetitive tasks, leading to significant efficiency gains and reduced operational costs. This automation frees up human employees to focus on more complex and strategic initiatives, ultimately boosting productivity and innovation. AI algorithms can also analyze vast amounts of data to identify patterns and insights that would be impossible for humans to discern, enabling businesses to make more informed decisions and anticipate future trends.
Optimizing Processes with Automation
Automation is no longer a futuristic concept; it's a present-day reality impacting numerous industries. From manufacturing and logistics to customer service and marketing, automation streamlines processes, enhancing efficiency and reducing errors. Automated systems can operate 24/7, minimizing downtime and maximizing output, leading to higher profitability. Furthermore, automation often leads to improved accuracy and consistency in tasks, ensuring quality control and reliability.
Harnessing the Power of Big Data
Big data analytics is a game-changer for businesses seeking to gain a competitive edge. By collecting, storing, and analyzing massive datasets, businesses can uncover valuable insights into customer behavior, market trends, and operational performance. These insights enable data-driven decision-making, leading to improved strategies and enhanced profitability. Organizations can leverage this data to personalize customer experiences and tailor products or services to meet specific needs, ultimately boosting customer satisfaction and loyalty.
Enhancing Security Measures with Cybersecurity
In today's interconnected world, robust cybersecurity measures are paramount for protecting sensitive information and maintaining business continuity. Implementing advanced security protocols and technologies is crucial for safeguarding data from cyber threats. Cybersecurity threats are constantly evolving, demanding proactive measures and a commitment to staying ahead of potential vulnerabilities. This involves regularly updating security systems, employing multi-factor authentication, and educating employees on best practices to prevent data breaches and maintain business integrity.
Embracing Cloud Computing for Scalability
Cloud computing offers unparalleled flexibility and scalability, enabling businesses to adapt to changing demands and expand operations efficiently. Cloud-based solutions provide access to resources on-demand, eliminating the need for significant upfront investments in hardware and infrastructure. This agility allows businesses to scale their operations quickly and easily in response to market fluctuations and growth opportunities. Cloud computing also enhances collaboration and data accessibility, facilitating seamless communication and information sharing across teams and departments.
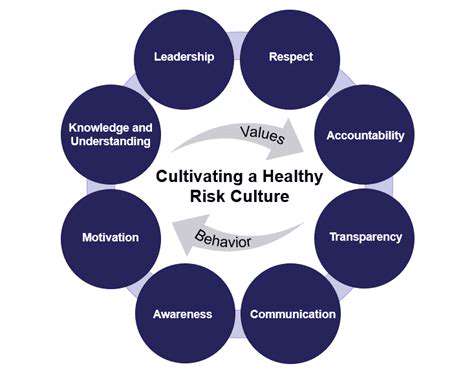
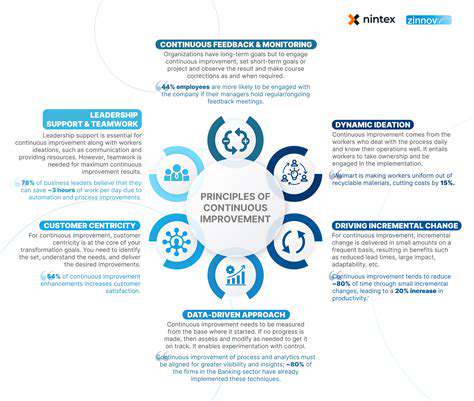
Investing in a Culture of Security and Continuous Improvement
Understanding the Foundation of a Secure Culture
A robust security culture isn't built overnight; it's a gradual process that requires a foundational understanding of the importance of security for everyone within the organization. This understanding encompasses not just technical aspects, but also the human element, recognizing that individuals are often the weakest link in the security chain.
Cultivating a proactive approach to security is paramount. Employees need to be empowered and educated to identify and report potential threats, fostering a sense of shared responsibility and accountability. This requires clear communication and consistent reinforcement of security policies and procedures.
Establishing Clear Policies and Procedures
Explicit, easily accessible, and regularly updated security policies are crucial to guiding employee behavior. These policies should outline acceptable use of company resources, including data and technology, while emphasizing the importance of data protection and confidentiality. Thorough training programs are essential for effective policy implementation.
Security policies must be consistently enforced to demonstrate commitment to a secure environment. This includes clear escalation procedures for reported incidents and a transparent process for addressing violations.
Promoting Security Awareness Training
Regular and engaging security awareness training is vital for equipping employees with the knowledge and skills needed to identify and respond to potential threats. This training should cover a range of topics, including phishing scams, social engineering tactics, and the importance of strong passwords.
These training programs should be tailored to different roles and responsibilities within the organization. Understanding the specific security risks relevant to each department is critical to ensure that training is relevant and impactful.
Fostering a Reporting Culture
Encouraging employees to report suspected security incidents is paramount to effective security management. A culture of open communication and trust must be cultivated, ensuring that employees feel safe and supported in reporting potential vulnerabilities without fear of retribution.
Creating an environment where employees feel empowered to report without fear is essential. This requires clear reporting channels, confidentiality assurances, and prompt investigation of all reported incidents. It's crucial to demonstrate that all reports are taken seriously and acted upon accordingly.
Implementing Robust Access Controls
Implementing robust access controls is critical to restricting unauthorized access to sensitive information and systems. This includes multi-factor authentication, strong password policies, and regular audits of user accounts.
Properly managing user access privileges is a key aspect of this process. Regularly reviewing and adjusting access rights based on employee roles and responsibilities is vital to maintain security effectively. Access control is not a one-time task, but a continuous process requiring ongoing vigilance.
Encouraging a Culture of Continuous Improvement
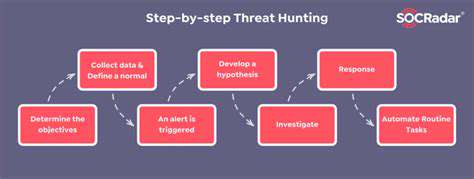
Security is an evolving landscape, and a culture of continuous improvement is essential to adapting to emerging threats. Regular reviews and assessments of security policies and procedures are necessary to ensure that they remain effective and relevant.
Regularly evaluating the efficacy of existing security measures and adapting to new threats is crucial. Staying ahead of the curve requires proactive monitoring of the threat landscape and incorporating new learning into security practices. This ensures the organization's security posture remains strong and resilient.
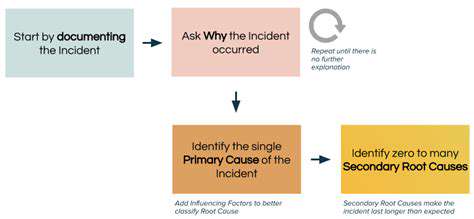
Addressing Security Breaches Effectively
Unfortunately, security breaches can occur despite best efforts. A crucial aspect of a strong security culture is a well-defined incident response plan, which outlines the steps to take in the event of a breach.
Swift and decisive action during a security breach is vital. This includes containment of the breach, notification of affected parties, and implementing measures to prevent similar incidents from happening again. Learning from the breach and adjusting security protocols is essential for future prevention.