Predictive Threat Modeling and Proactive Security
Understanding Predictive Threat Modeling
Predictive threat modeling is a proactive approach to security that goes beyond simply identifying vulnerabilities. It involves analyzing potential future threats based on historical data, emerging trends, and technological advancements. This analysis allows organizations to anticipate and mitigate potential risks before they materialize, rather than reacting to incidents after they occur. By understanding the evolving threat landscape, organizations can proactively strengthen their defenses and significantly reduce their exposure to cyberattacks. This approach requires a deep understanding of the organization's systems and data, as well as a thorough analysis of potential attack vectors.
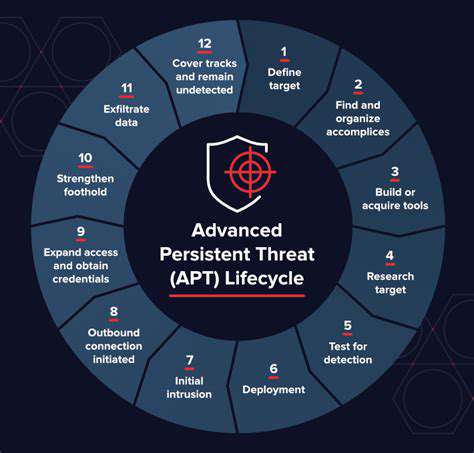
A crucial aspect of predictive threat modeling is the identification of potential attack vectors. This involves scrutinizing various avenues through which malicious actors might gain unauthorized access to sensitive information or disrupt critical operations. Analyzing historical security incidents, known attack patterns, and emerging vulnerabilities is paramount to anticipating future threats. Developing a framework that allows for continuous adaptation and refinement based on evolving threats is essential for effective predictive threat modeling.
Leveraging AI for Enhanced Threat Detection
Artificial intelligence (AI) plays a critical role in enhancing predictive threat modeling. AI algorithms can analyze vast amounts of data, including security logs, network traffic, and user behavior, to identify anomalies and patterns indicative of potential threats. This capability allows for the rapid detection of suspicious activities that might otherwise go unnoticed by traditional security systems. By automating the threat detection process, AI can significantly improve response times and reduce the window of opportunity for attackers.
Machine learning models can be trained on historical data to learn and adapt to evolving threat patterns. This continuous learning process enables AI to identify emerging threats and adapt security measures accordingly. The ability of AI to learn and adapt is crucial for maintaining effective threat modeling in a rapidly changing technological landscape.
Proactive Security Measures Based on Predictions
Predictive threat modeling enables organizations to implement proactive security measures. By anticipating potential threats, organizations can strengthen their defenses and reduce the likelihood of successful attacks. This includes implementing robust access controls, enhancing security protocols, and regularly patching vulnerabilities. Proactive measures can include educating employees about common threats and best practices for data security, which can significantly reduce the risk of phishing attacks and other social engineering schemes. Proactive measures, based on predictive threat modeling, are essential for maintaining a strong security posture.
Implementing a Predictive Security Framework
Developing a comprehensive predictive security framework is essential for successful implementation. This framework should incorporate clear guidelines and procedures for identifying potential threats, assessing risks, and implementing mitigation strategies. The framework should also outline roles and responsibilities for each team member involved in the security process. Effective communication and collaboration between different teams are vital for a successful predictive security framework. The framework should also include a mechanism for regular review and updates to ensure that it remains relevant and effective in the face of evolving threats.
Continuous Monitoring and Improvement
Predictive threat modeling is not a one-time exercise; it requires continuous monitoring and improvement. Organizations must consistently analyze new data, identify emerging threats, and adapt their security strategies accordingly. Regular security audits and penetration testing are crucial for identifying vulnerabilities and ensuring the effectiveness of implemented security measures. Regular training and awareness programs for employees are also necessary to maintain a strong security culture. Through continuous monitoring, organizations can adapt to the evolving threat landscape and ensure the effectiveness of their proactive security measures.