The Future of Security Analytics: Integration and Automation

Predictive Modeling and AI
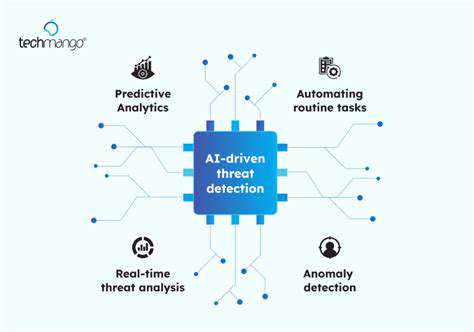
The future of security analytics is undeniably intertwined with the power of predictive modeling and artificial intelligence. These technologies allow us to move beyond simply reacting to security incidents and proactively anticipate potential threats. By analyzing vast datasets of historical security events, AI algorithms can identify patterns and anomalies that might indicate impending attacks. This proactive approach is crucial in today's rapidly evolving threat landscape, where attackers constantly develop new and sophisticated techniques.
Predictive models can also be used to prioritize security alerts, focusing resources on the most critical threats. This intelligent prioritization is essential for security teams to effectively manage their limited resources and respond efficiently to emerging risks. Security analytics will be significantly enhanced by the ability to anticipate threats before they materialize.
Enhanced Threat Detection and Response
Future security analytics solutions will be characterized by a significant enhancement in threat detection and response capabilities. This means moving beyond simple signature-based detection to more sophisticated techniques that can identify zero-day exploits and advanced persistent threats (APTs). These advanced capabilities will be necessary to address the ever-increasing sophistication of cyberattacks.
Improved detection methods will rely heavily on machine learning and behavioral analytics. These techniques will be able to identify subtle deviations from normal user or system behavior, which can indicate malicious activity. This shift towards behavioral analytics is crucial for detecting threats that bypass traditional signature-based defenses.
Data Visualization and Accessibility
Effective security analytics relies heavily on the ability to understand and interpret complex data. Future systems will prioritize clear and intuitive data visualization tools that allow security analysts to quickly grasp the overall security posture and identify potential vulnerabilities. This improved visualization will empower analysts to make faster, more informed decisions in response to potential threats.
Furthermore, enhanced accessibility to security data will be paramount. Security information and event management (SIEM) systems of the future will need to provide analysts with the tools to easily access and analyze data from a wide range of sources, including cloud environments and IoT devices. This accessibility will be critical for maintaining a comprehensive view of the entire security landscape.
Improved Collaboration and Automation
The future of security analytics demands enhanced collaboration between security teams and other departments. This interdepartmental collaboration will be crucial for proactive threat hunting and incident response. Integrating security analytics with other business systems will provide a holistic view of potential risks, allowing organizations to take a more comprehensive approach to security.
Automation will play a vital role in streamlining security operations. Automated threat detection, incident response, and remediation processes will reduce the workload on security analysts, allowing them to focus on more complex and strategic tasks. This automation will improve efficiency and reduce response times to threats, ultimately strengthening overall security posture.