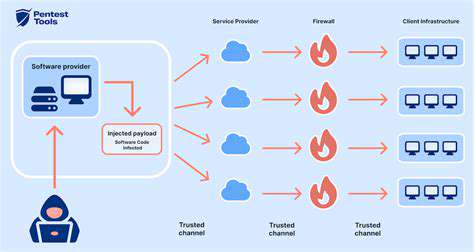
The Limitations of Perimeter Security
Traditional security models rely heavily on the concept of a secure perimeter, treating anything outside that boundary as inherently hostile. This approach, while effective in simpler environments, struggles to adapt to the complexities of today's interconnected and dynamic digital landscape. The rise of cloud computing, remote workforces, and sophisticated cyberattacks has exposed the vulnerabilities inherent in this outdated strategy, highlighting the need for a more comprehensive and proactive approach to security management.
Organizations relying solely on perimeter security often find themselves ill-equipped to address the evolving threat landscape. Attackers are increasingly adept at bypassing traditional firewalls and intrusion detection systems, exploiting vulnerabilities in applications and user endpoints. This demonstrates a fundamental weakness in the paradigm, as it fails to account for the inherent risks associated with users, devices, and applications, regardless of their location within the network.
Embracing a Zero Trust Framework
The Zero Trust security model offers a compelling alternative to the traditional perimeter-based approach. It operates on the principle of never trust, always verify, meticulously validating every user, device, and application access request, regardless of its location within or outside the organization's network. This granular approach acknowledges that threats can originate anywhere, even from within the network itself.
By implementing a Zero Trust framework, organizations can significantly enhance their security posture by reducing attack surface and strengthening overall security controls. This shift in mindset emphasizes the importance of continuous authentication and authorization to ensure that only authorized users and devices can access sensitive data and resources.
The Importance of Identity and Access Management
In a Zero Trust environment, robust identity and access management (IAM) systems play a crucial role in establishing trust and controlling access. Effective IAM solutions allow organizations to identify and verify users and devices accurately, providing granular control over access privileges based on context and role.
This granular control extends to the specific data and applications that users and devices can access, preventing unauthorized access even if a compromised device or account manages to penetrate the network perimeter. This level of precision and control is essential in mitigating the risk of insider threats and malicious actors.
Implementing Zero Trust Principles: A Multi-Layered Approach
Implementing Zero Trust requires a multi-layered approach that encompasses various security technologies and processes. This includes the use of micro-segmentation, network segmentation, and the implementation of strong authentication methods like multi-factor authentication (MFA) to reinforce the security of sensitive data and critical infrastructure.
Furthermore, organizations need to establish clear policies and procedures for access requests, user roles, and device management, ensuring that access rights are appropriately managed and continuously monitored. Continuous monitoring and adaptive response mechanisms are crucial for mitigating threats and adapting to evolving security needs.
Cultural Shift and Employee Training
Adopting a Zero Trust framework necessitates a cultural shift within an organization. Employees need to understand the importance of security protocols and the implications of violating them. Comprehensive training programs are essential to ensure that all personnel are aware of the new security policies and procedures and can effectively comply with them.
The Business Value Proposition of Zero Trust
Beyond the enhanced security posture, a Zero Trust framework brings tangible business value. By reducing the risk of data breaches and mitigating the impact of security incidents, organizations can protect their reputation, maintain customer trust, and avoid significant financial losses associated with data breaches and compliance penalties. This proactive approach to security strengthens the overall resilience of the organization and fosters a more secure and productive digital environment.
Beyond the Network: Verifying Every Interaction

Ensuring Data Integrity
Data integrity is paramount in today's interconnected world. Reliable verification processes are crucial to ensure that the information being transmitted and stored is accurate and trustworthy. This is particularly important in sensitive applications like financial transactions and healthcare records, where errors can have significant consequences. Robust verification mechanisms are essential to mitigate risks and maintain public confidence in the data.
Verification methods should be carefully designed and implemented to prevent unauthorized modifications or tampering. This includes employing cryptographic techniques, secure storage protocols, and regular auditing procedures to detect any anomalies or discrepancies.
Understanding the Role of Validation
Validation plays a vital role in the verification process. It involves confirming that the data conforms to predefined rules and standards. This step helps to identify and correct any inconsistencies before they propagate through the system. A robust validation process ensures that the data meets the required criteria, preventing errors from entering the system and contaminating the overall data integrity.
Furthermore, validation is a key element in ensuring data quality and reliability. By ensuring compliance with established rules and standards, validation helps maintain consistency and accuracy throughout the entire data lifecycle.
The Importance of Security Protocols
Implementing robust security protocols is critical to safeguarding data integrity. These protocols should incorporate encryption, access controls, and authentication mechanisms to protect the data from unauthorized access or modification. Comprehensive security protocols are essential to prevent data breaches and maintain the confidentiality and privacy of sensitive information. Regular security audits and penetration testing are also important to identify and address potential vulnerabilities in the system.
Verification in the Cloud Environment
In the cloud environment, data verification presents unique challenges. Distributing data across multiple servers and locations requires sophisticated verification mechanisms to ensure data consistency and integrity. Cloud-based verification systems need to be scalable and resilient to handle large volumes of data and potential outages. The verification process must also be adaptable to evolving cloud architectures.
The Significance of User Authentication
User authentication is a critical component of data verification. Strong authentication methods are essential to verify the identity of users accessing sensitive information. This helps prevent unauthorized access and maintains the security and integrity of the data. Multi-factor authentication is often employed to enhance the security posture.
Continuous Monitoring and Auditing
Continuous monitoring and auditing are crucial for ongoing verification efforts. Regular monitoring helps to detect any anomalies or unauthorized activities in real-time. Auditing trails provide an historical record of data access and modifications, enabling effective investigation and resolution of any issues. This proactive approach allows for timely intervention and prevents potential data breaches or integrity issues. Regular reviews of security measures are vital to ensure that they remain effective and up-to-date.
Building a Culture of Security Awareness
Cultivating a Security-Conscious Environment
Building a culture of security awareness is not a one-time event; it's an ongoing process that requires consistent effort and a commitment from every member of the organization. Creating a safe and secure workplace environment requires a proactive approach that goes beyond simply issuing policy documents. It involves fostering a sense of shared responsibility and encouraging employees to actively participate in maintaining security protocols.
This proactive approach should be integrated into the everyday work routines. Regular training sessions, clear communication channels, and readily available resources are crucial for ensuring employees understand the potential risks and how to mitigate them. Furthermore, employees should be empowered to report suspicious activity without fear of retribution.
Establishing Clear Communication Channels
Effective communication is paramount to fostering a culture of security awareness. Employees need to be kept informed about current threats, security policies, and best practices. This includes regular updates through newsletters, internal forums, or dedicated intranet sections. Clear and concise language is essential to ensure that the information is easily understood by everyone.
A system for reporting security incidents or concerns should be easily accessible and well-documented. This system should be user-friendly and include clear steps on how to report issues. Prompt response and investigation of reported incidents are vital for maintaining trust and demonstrating that security concerns are taken seriously.
Implementing Regular Training and Awareness Programs
Regular training programs are essential for keeping employees informed about the latest security threats and best practices. These programs should be tailored to the specific roles and responsibilities of each employee, covering topics such as phishing scams, social engineering tactics, and the importance of strong passwords. Training should be interactive and engaging, using real-world scenarios and practical examples to help employees better understand the potential risks.
Beyond initial training, ongoing reinforcement is crucial. This can be achieved through refresher courses, reminders, and interactive exercises. Security awareness campaigns can also be implemented to raise awareness of specific threats or vulnerabilities. Regular testing of employee knowledge through quizzes or simulations can help identify areas where further training is needed.
Promoting a Culture of Reporting and Feedback
Creating a culture where employees feel comfortable reporting security incidents or concerns is essential. This involves establishing clear reporting channels, ensuring confidentiality, and providing mechanisms for feedback. Employees should understand that their reports are valued and will be handled with discretion.
Encouraging open dialogue and feedback is critical. Regular feedback sessions and surveys can provide valuable insights into employee perceptions and concerns related to security. This feedback can be used to refine security policies and procedures, making them more effective and relevant. This ongoing dialogue can also help build trust and foster a sense of shared responsibility for security within the organization.
Implementing Zero Trust: A phased approach for successful transition
Understanding the Zero Trust Model
Zero Trust security is a security model that assumes no implicit trust, regardless of whether a user or device is inside or outside a network perimeter. Instead, it verifies every user and device requesting access to resources, assessing their risk posture in real-time. This contrasts with traditional network security models that often rely on a perimeter-based approach, trusting users and devices once they're inside the network. Implementing a Zero Trust model requires a fundamental shift in security thinking, moving from a broad trust assumption to a granular, continuous verification process.
This approach is increasingly important in today's dynamic threat landscape where attackers are constantly finding new ways to exploit vulnerabilities. Zero Trust requires a comprehensive understanding of your organization's assets and access patterns to create a secure and resilient environment.
Phase 1: Assessment and Planning
The initial phase of implementing Zero Trust involves a thorough assessment of your current security infrastructure, identifying vulnerabilities, and defining clear objectives for the transition. This requires a detailed inventory of your network resources, including devices, applications, and users. Crucially, it also entails understanding your organization's security policies and compliance requirements to ensure that the Zero Trust framework aligns with existing standards.
Phase 2: Policy Development and Segmentation
Developing robust access policies is a critical step. This involves defining granular access controls based on the principle of least privilege. This means granting users and devices only the necessary access to resources, nothing more. Simultaneously, segmenting your network into smaller, isolated zones limits the impact of a potential breach. This segmentation helps to contain any compromise, preventing its lateral movement across the network.
Phase 3: Identity and Access Management (IAM) Enhancements
Zero Trust fundamentally relies on strong authentication and authorization mechanisms. This phase focuses on enhancing your existing Identity and Access Management (IAM) system to support the granular access controls required by Zero Trust. This might involve implementing multi-factor authentication (MFA) for all users, regardless of location. Implementing strong password policies, and regularly reviewing and updating access controls are essential elements for success.
Phase 4: Network Segmentation and Micro-segmentation
Network segmentation is a crucial element of Zero Trust. Dividing the network into smaller, isolated segments limits the impact of a breach. Micro-segmentation takes this further, segmenting down to the level of individual servers and applications. This approach helps to control the flow of traffic and isolates resources to contain any potential compromise. This level of granular control is essential for containing threats and minimizing the blast radius of a successful attack.
Phase 5: Endpoint Security and Device Posture
Ensuring that all devices accessing your network are secure and compliant is paramount in a Zero Trust environment. This involves implementing robust endpoint security measures, including anti-malware, intrusion detection systems, and real-time threat monitoring. Regularly assessing the posture of devices is essential to ensure that they meet the organization's security policies and standards.
Phase 6: Continuous Monitoring and Improvement
Implementing a Zero Trust model is not a one-time project but an ongoing process of continuous improvement. This phase involves establishing mechanisms for monitoring the effectiveness of the Zero Trust framework, identifying potential vulnerabilities, and adapting the policies and controls to match evolving threats. Regular security audits, threat intelligence analysis, and feedback loops from security operations are crucial elements in ensuring the ongoing success and resilience of the Zero Trust framework.