Immersive learning environments are transforming the way students interact with educational content. These innovative approaches leverage technology to create engaging and interactive experiences that go beyond traditional methods of instruction. By immersing learners in simulated environments, students can explore complex concepts, practice skills, and develop critical thinking abilities in a safe and supportive setting.
Recovery Planning and Disaster Preparedness
Understanding the Need for Recovery Planning
Effective recovery planning is crucial for organizations facing ransomware attacks. It's not just about restoring data; it's about mitigating the damage, minimizing downtime, and ensuring business continuity. A well-defined plan outlines the steps to follow during and after an incident, from initial detection to full restoration. This includes identifying critical systems, data, and processes, and establishing clear communication channels for all stakeholders. Proactive planning ensures a more organized and efficient response, reducing the negative impact on operations and reputation.
Failing to plan is planning to fail. A well-thought-out recovery plan serves as a roadmap for navigating the complexities of a ransomware attack, guiding decision-making and resource allocation during a crisis. It ensures that the organization is prepared to minimize the disruption to business operations, recover data and systems as quickly as possible, and maintain the trust of customers, partners, and stakeholders. This proactive approach is essential for minimizing the long-term consequences of a ransomware attack.
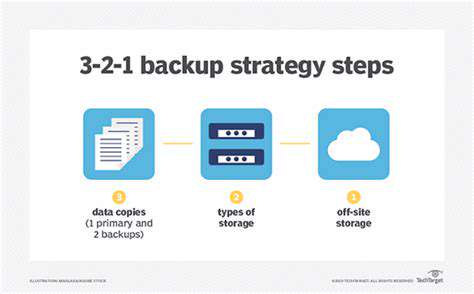
Developing a Robust Backup Strategy
A robust backup strategy is the cornerstone of any recovery plan. Regular, automated backups are essential to ensure data can be quickly restored. This includes backing up not just critical data but also the entire operating system and applications. The backup process should be tested regularly to verify its functionality and ensure that data can be effectively restored within a reasonable timeframe. Implementing a multi-layered backup approach, including cloud and on-site backups, can provide additional protection against data loss.
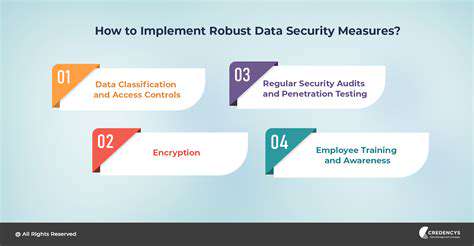
Implementing Data Encryption and Access Controls
Data encryption and strong access controls are vital security measures for preventing ransomware attacks and limiting the damage if one occurs. Encrypting sensitive data both at rest and in transit makes it unusable to attackers even if they gain access. Implementing multi-factor authentication and least privilege access controls restricts unauthorized access to sensitive data and systems. These measures significantly reduce the likelihood of successful attacks and limit the potential impact on critical data and systems.
Regular Security Audits and Vulnerability Assessments
Regular security audits and vulnerability assessments are critical for identifying and addressing potential security weaknesses in systems and networks. These assessments help organizations proactively identify vulnerabilities before they can be exploited by attackers. By regularly reviewing and updating security protocols, organizations can strengthen their defenses against ransomware attacks and other cyber threats. Regular patching of software and systems is an integral part of this process, ensuring that known vulnerabilities are promptly addressed.
Data Recovery and Business Continuity Planning
Data recovery and business continuity planning are intertwined. A robust data recovery plan outlines the steps to restore data and systems after a ransomware attack. This includes identifying recovery points, establishing recovery procedures, and practicing recovery scenarios. A business continuity plan details how the organization will maintain critical operations during and after an incident. This includes identifying alternative locations, processes, and personnel to ensure minimal disruption. This comprehensive approach helps ensure that the organization can continue functioning effectively despite disruptions.
Testing and Maintaining the Recovery Plan
Regular testing and maintenance are crucial for ensuring the effectiveness of the recovery plan. This includes conducting regular drills and simulations to identify potential weaknesses and make necessary adjustments. Regular reviews of the plan, in light of emerging threats and vulnerabilities, are essential for maintaining its relevance and effectiveness. Continuous improvement is key to maintaining a resilient and adaptable approach to disaster preparedness, ensuring that the organization is best positioned to respond effectively to any future ransomware attacks.